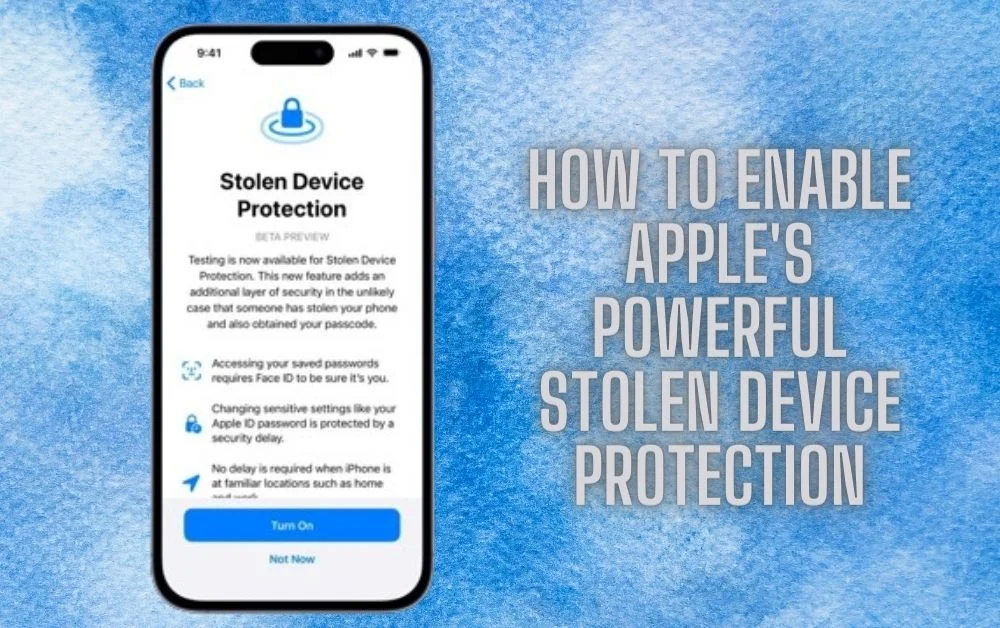
How to Enable Apple’s Powerful Stolen Device Protection 2024: Enhancing Security
Learn How to Enable Apple’s Powerful stolen device protection 2024 effortlessly. Safeguard your valuable Apple devices with the latest security features. Stay ahead of potential threats, secure your data effectively, and utilize stolen device protection to prevent unauthorized access. Discover the steps to activate this enhanced protection on all your Apple products for peace of mind. Key Takeaways Enable Apple’s Stolen Device Protection: Take proactive steps to enable Apple’s powerful stolen device protection feature to safeguard your device in case of theft. Utilize Biometric Authentication: Implement biometric authentication methods like Face ID or Touch ID to add an extra layer of security to your device. Stay Updated with iOS: Regularly update your iOS to ensure that you have the latest security features and enhancements for optimal device protection. Manage Actions Carefully: Be cautious with actions taken on your device once stolen device protection is enabled to prevent unauthorized access or misuse. Enhance Overall Security: Enhance your device’s overall security by combining stolen device protection with other security measures like strong passwords and two-factor authentication. Actively Protect Your Device: By understanding, enabling, and enhancing Apple’s stolen device protection, you actively protect your valuable Apple devices from potential theft. Understanding Stolen Device Protection Safeguarding Your Devices Stolen device protection is crucial for securing your Apple devices from unauthorized access. By enabling stolen device protection, you can prevent thieves from using or accessing your stolen gadgets. This feature adds an extra layer of security, ensuring that even if your device gets into the wrong hands, it remains inaccessible. Enabling stolen device protection on your Apple devices involves activating features like Find My iPhone/iPad/Mac. These tools allow you to locate a lost or stolen device remotely, lock it with a passcode, display a custom message on the screen, and even erase all data if necessary. By understanding how these functions work together under the stolen device protection section, you can better protect your personal information and privacy in case of theft. Enabling Stolen Device Protection for Apple Devices Tracking and Locating Your Device Enabling stolen device protection on your Apple devices allows you to utilize features like Find My iPhone/iPad/Mac. These tools help you track and locate your lost or stolen device easily. By activating this feature, you can pinpoint the exact location of your device using GPS technology. Apple’s built-in tracking system lets you see the real-time location of your device on a map. This functionality is crucial in situations where your phone or laptop has been misplaced or stolen. With just a few clicks, you can access the location information through the Find My app on another Apple device or through iCloud.com. Remote Locking and Erasing Data One significant benefit of enabling stolen device protection is the ability to remotely lock and erase data from your missing device. In case you cannot retrieve it physically, locking it prevents unauthorized access to sensitive information stored on the device. Moreover, if recovery seems unlikely, remotely erasing all data ensures that your personal information remains secure. Implementing Biometric Authentication Enhanced Security Biometric authentication like Touch ID and Face ID provides an added layer of security to your Apple device. By setting up biometric authentication, only authorized users can access the device, ensuring that your personal information remains protected. This feature prevents unauthorized individuals from gaining access to your phone or tablet. Pros: Enhanced security measures. Protection against unauthorized access. Implementing biometric authentication not only safeguards your device but also secures sensitive data stored on it. With this technology in place, you can prevent others from unlocking your phone or making purchases without authorization. For instance, if someone steals your iPhone with Face ID enabled, they won’t be able to unlock it without presenting your face. User-Friendly Access Biometrics streamline the process of unlocking devices by eliminating the need for passcodes or patterns. Users can simply use their fingerprint (Touch ID) or facial recognition (Face ID) to unlock their devices quickly and conveniently. This makes accessing the device more efficient and user-friendly. Cons: Dependency on specific hardware for functionality. Possible privacy concerns related to storing biometric information. Managing Actions with Protection Enabled Performing Certain Actions When you have stolen device protection enabled on your Apple device, you can carry out certain actions to help in various scenarios. For instance, you can play a sound to locate your misplaced device easily. This feature is handy when you’ve lost your phone nearby and need an audible cue. Displaying a message on the lock screen of your lost device is another useful function. You can input contact information or a reward offer for the finder to see. This way, if someone finds your lost phone, they know how to reach you. Enhancing Recovery Chances Effectively managing these actions significantly boosts the chances of recovering your missing or stolen Apple gadget. By remotely wiping sensitive data from your device using these features, you ensure that even if the physical device cannot be retrieved, personal information remains secure. Moreover, these actions facilitate communication with whoever may have found or taken possession of your Apple product. Clear instructions displayed via messages could prompt the finder to return it willingly. iOS Updates Impact on Device Protection Security Enhancements Regular iOS updates are crucial for enhancing the security features of your Apple device. These updates often include improvements to stolen device protection, making it harder for thieves to access or misuse stolen devices. For example, recent updates have introduced features like Activation Lock, which requires the original owner’s Apple ID and password to activate a device after being remotely erased. Apple continuously works on fixing vulnerabilities and strengthening security measures through these updates. By enabling automatic updates on your device, you ensure that you benefit from the latest security enhancements promptly. This proactive approach significantly reduces the risk of unauthorized access or data breaches in case your device gets lost or stolen. Importance of Updating Keeping your Apple device up to date with the latest iOS version is essential for maintaining robust security features … Read more